Phishing prevention and email hygiene
2022-06-04 08:07

by Harlo Holmes -Chief Information Security Officer and Director of Digital Security
Phishing prevention and email hygiene
Most people are hacked via phishing attacks. Here's how to better protect yourself.
Journalists and newsrooms are increasingly the victims of hacking and malware, and often hackers target them through their email. Virtually every "sophisticated" hack of an individual reporter or entire newsroom involves a relatively simple attack: phishing and spear phishing.
Phishing is a social-engineering attack where an adversary crafts an email (or text, app message) in such a way to trick you into divulging information that could be used against you or your network; gain access to, and ultimately commandeer your account; or introduce malware and/or viruses to your machine. Spear phishing is just like phishing, except the attacker uses information he or she already knows about you to specially tailor their phishing email. There are plenty of ways to be phished, and it happens incredibly frequently. Prepare yourself with our guide to mitigate or avoid phishing or spear phishing attacks.
2FA to the rescue
One of the most important advances in credential security is two-factor authentication. Two-factor authentication (or “2FA”) relies on the idea that services are more secure if you access them with something you know (i.e., your passphrase), and something you have (i.e. physical access to your phone). With 2FA, each log in will require an extra step after you input your password: you’ll be prompted to enter a code that is displayed only on the device you have control over. This code can come to you via text message (i.e. SMS) from the service itself, or is displayed in an app on your phone (such as Google Authenticator or Authy). That way, if someone ever gets your password, they still could not log in as you unless they had physical control over your phone as well.

Turn on two-factor authentication for any and all services that you can, starting with your Gmail account. Better yet, get a security key, a small device that you either plug into your computer, or connect to your phone wirelessly, if it supports NFC, to enable this securely.
In the event that you get phished (it happens to the best of us!) no one will be able to make use of the stolen password because they would also need to have access to your security key to log into that account.
The website 2fa.directory has an exhaustive list of services that support 2FA, as well as direct links to directions for enabling it everywhere it’s available.
Sometimes, the "from" field is lying to you
Understand that things like the "from" field in your emails can be forged to trick you. While it’s difficult for someone to send an email using someone else’s address, it can be done. It’s also incredibly easy to create an email address that is similar enough to your contact’s email to impersonate them.
In the first case, scrutinizing the email headers might tip you off to a forgery. However, not all email clients make this clear, or alert you to when someone is attempting to trick you this way. Here’s an example of this attack in action: an email claiming to come from a legitimate gmail address arrives in my inbox, but was not sent from one of Gmail’s real servers. This is why there is a yellow phishing warning at the top of the message.
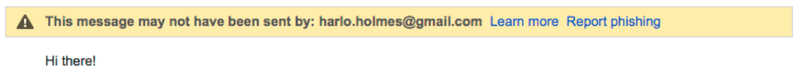
Information in the source of an email cannot be easily forged, and so that bit of information is more trustworthy than the name/email address associated with the email. Be aware of this threat, and choose an email client that has your protection in mind. As much as we may criticize Google for being a huge monolith that mines your personal data for ad revenue, Google provides a lot of protection against this attack.
The second case concerns a trick called typo-squatting: when someone purchases a domain that looks a lot like a legitimate domain you’re familiar with, but it’s misspelled just a bit to trick you. For example, I once received an email from someone at the "gooogle" domain (notice the 3 o’s?!) That was a phishing attempt that wanted me to log into their phony site to steal my real Google credentials.
Beware attachments
E-mail attachments can carry malware and viruses, and commonly accompany phishing emails. The best way to avoid malware from attachments is to never download them. However, downloading documents is often part of a journalist’s job. As a cardinal rule, don’t open any attachments immediately, especially if they come from people you do not know. If your source is sending you a document that’s mostly text, like a copy of a memo, ask them to copy-paste the text in the email instead of sending it as an attachment.
If you have to open the attachment, it should only be opened in a "sandboxed" environment: a program, service, or even a dedicated computer that enforces separation between documents you open and the computer you use. Google Drive from within your browser can be a very efficient sandbox. So instead of downloading an attachment and opening it on your computer, view it there.
If you are really suspicious but still need to open the attachment, you could also use an “airgapped” machine (a computer that never touches a network) to view documents, and print out the ones you need for later. (Also, have a look at our guide for using the Tails operating system for such a task).
On the other hand, sometimes bad actors will send you attachments you have no intention of viewing, and those are likely to contain malware. Usually, these attachments include (but aren’t limited to) JavaScript (.js/.jse) files, or Windows Script files (.wsh/.wsp). Your computer might run these files automatically, and that’s one way malware gets into your computer.
Change your settings so that certain files never run automatically, but instead open up in a text editor application, which will display the file’s contents instead of running it. Ideally, whichever text editor you use should not sync to the cloud, just in case it’s actually a legitimate file you don’t want to share with a snoopy cloud provider.
On Windows:
- Open an Explorer window and do a search for the type of file you wish to change (“.js” for example).
- Right-click on a resulting file, and select “Open With -> Choose another app.”
- If Notepad or another app you want is listed, select it. If not, choose “Look for another app on this PC” to find and select the app you want to use instead.
- Check “always use this app to open .js files” (using .js files as an example).
- Finally, select “OK” to save your changes.
While this is usually less of an attack vector for Mac users, here’s how to change a file’s default application on a Mac.
On a Mac:
- Open a Finder window and do a search for the type of file you wish to change (“.js” for example).
- Control-click on a resulting file, and select “Get Info.”
- Change the “Open with:” option to your text editor of choice.
- Click “Change All…” so each file of that type will open in the same way.
Click with caution
Be skeptical of links in emails. There’s a simple trick for making sure a link in an email will send you to where it’s supposed to: use your mouse to hover over any link before clicking on it, to see what the actual address is. If you’re using a mobile device, a “long press” will also show the real address.

If it’s a link shortener (e.g., a site like bit.ly which takes long web addresses and makes a short, typable one) instead of the full address, don’t open it. Furthermore, don’t follow links to domains you are unfamiliar with. If in doubt, perform a search for the domain, with the domain name in quotation marks with a privacy-preserving search engine (like DuckDuckGo) to see if it’s a legitimate web site. This isn’t a 100% fix, but it’s a good precaution to take.

Finally, if you click on any link from an email, and are asked to log in — a common endgame for phishing campaigns, do not do it. Instead, manually go to the website of the service you are trying to log into and log in there. This way, you’ll know you’re logging in to the correct website because you’ve typed in the address for it, rather than having to trust the email link.
In-line images are little tracking beacons
Turn off your email client’s ability to display images automatically. Whenever an image is loaded into your email display, a request is made to wherever on the internet that image is hosted. Adversaries have cribbed this play from the marketing industry: they use this trick to find out who has opened their email and when — kind of like a tracking beacon. Gmail has the option to prevent images from loading automatically — turn this on immediately! Here’s how: navigate to "Settings" from the gear icon at the right of the page and then “See all settings”. In the "General" tab (which is the first tab), select "Ask before displaying external images". Finally, click “Save changes.”

You can always enable images to load per email, or even per sender, if you trust the sender and want to view images in their email.
Stand up for yourself and others!
If anyone is sending you unsolicited attachments, links, or images, and seems suspiciously insistent that you open them immediately, kindly tell them to "go fly a kite!" Not only is what they’re doing rude, it could indicate that they intend to trick you, and are using social pressure to get you to complete their exploit. On the other hand, be mindful of these tricks, and try not to barrage people with links, images, and attachments in your email communications that would make your own real emails seem suspect. Not only does it show that you care about the safety of the people you communicate with, but it encourages a culture among your connections that is alert, aware, considerate, and privacy-forward.
Photo by Hivint. CC BY 2.0